What Is Malware Protection?
Malware, short for malicious software, is a term used to describe any software or code that is designed to harm, exploit, or compromise a computer system without the user’s knowledge or consent. It can take many forms and spread through various means, including email attachments, infected websites, or networks. Malware Protection refers to the measures taken to prevent, detect, and remove malware from computer systems and networks. Malware, short for malicious software, is any software designed to harm, steal data from, or otherwise disrupt computer systems or networks. It can take many forms, including viruses, trojans, worms, ransomware, spyware, and adware.
Adequate Ransomware Protection requires a multi-layered approach that includes technical controls, user awareness, and proactive security measures. Technical controls include antimalware software, firewalls, intrusion detection and prevention systems, and application-allow listing. User awareness includes educating employees on safe computing practices, such as not opening unsolicited emails to prevent Email Spoofing or downloading software from untrusted sources. Finally, proactive security measures include regular security assessments, vulnerability scanning, and penetration testing.
Common Types of Malware
Some of the most common Types of Malware include:
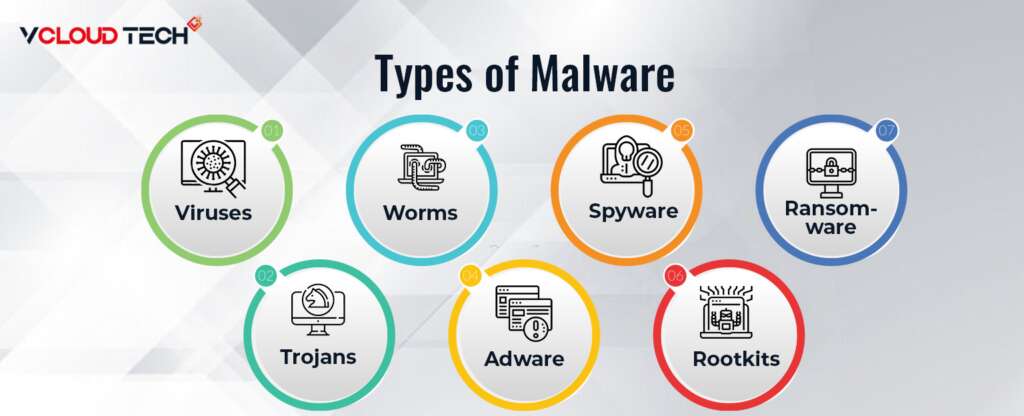
Viruses:
Viruses are one of the oldest and most well-known types of malware. They are self-replicating programs that infect other files on a computer or network and spread from system to system through various means, such as email due to lack of Email Security or file sharing. Once a virus infects a system, it can cause a range of problems, including data loss, system crashes, and the theft of personal information.
Trojans:
Trojans are malware programs disguised as legitimate software, but once installed, they allow attackers to gain unauthorized access to a system. They are often used to create backdoors into a system, allowing attackers to steal sensitive data or install other malware.
Ransomware:
It is a type of malware that encrypts a victim’s files and demands payment for the decryption key. Ransomware attacks have become increasingly common in recent years and can cause significant damage to individuals and businesses.
Worms:
Worms are self-replicating malware programs that spread from system to system without human intervention. They are often used to exploit vulnerabilities in operating systems and can cause significant damage to networks.
Adware:
Adware is malware that displays unwanted advertisements on a victim’s computer or mobile device. While not necessarily harmful, the adware can be highly annoying and slow down a system’s performance.
Spyware:
Spyware is a malware designed to steal sensitive information from a victim’s computer or mobile device. That can include personal information, usernames and passwords, and sensitive business data.
Rootkits:
Rootkits are a type of malware that is designed to hide their presence on a victim’s system. Attackers often use them to gain access to sensitive information or to create backdoors into a system.
How to Prevent Malware Infections in Your Organization?
Malware infections can cause significant damage to an organization’s data, systems, and reputation. Therefore, it is essential to take proactive measures to prevent malware infections. Here are some best practices for avoiding malware infections in your organization:
Use Antimalware Software:
One of the most critical steps in preventing malware infections is to install and maintain up-to-date antimalware software on all systems. This software should be configured to automatically update and scan systems regularly to detect and remove any malware infections.
Keep Software Up to Date:
Malware often exploits vulnerabilities in software to infect systems. Therefore, keeping all software up to date with the latest security patches and updates is crucial.
Use Strong Passwords:
Weak passwords can be easily compromised, providing attackers easy access to systems and data. Therefore, using strong passwords that are difficult to guess and changing them regularly is essential.
Implement Network Segmentation:
Network segmentation can help limit the spread of malware by isolating infected systems from the rest of the network. By dividing the network into smaller segments and controlling access between them, you can limit the impact of malware infections.
Educate Employees:
Many malware infections occur due to human error, such as opening a suspicious email attachment or visiting a malicious website. Therefore, educating employees on safe computing practices, such as not clicking on links or attachments in unsolicited emails, avoiding downloading software from untrusted sources, and being wary of social engineering attacks, is crucial.
Use Firewalls:
Firewalls can help block incoming traffic from known malicious IP addresses or domains. By preventing malware from reaching systems in the first place, Firewalls can help reduce the risk of infection.
Implement Access Controls:
Access controls can help limit the impact of malware infections by restricting the actions that users can take on a system. For example, implementing least privilege access can help prevent malware from spreading by limiting the ability of infected accounts to access other parts of the network.
How Does Antimalware Software Work?
Antimalware software detects and removes malicious software, such as viruses, trojans, and worms, from a computer or network.
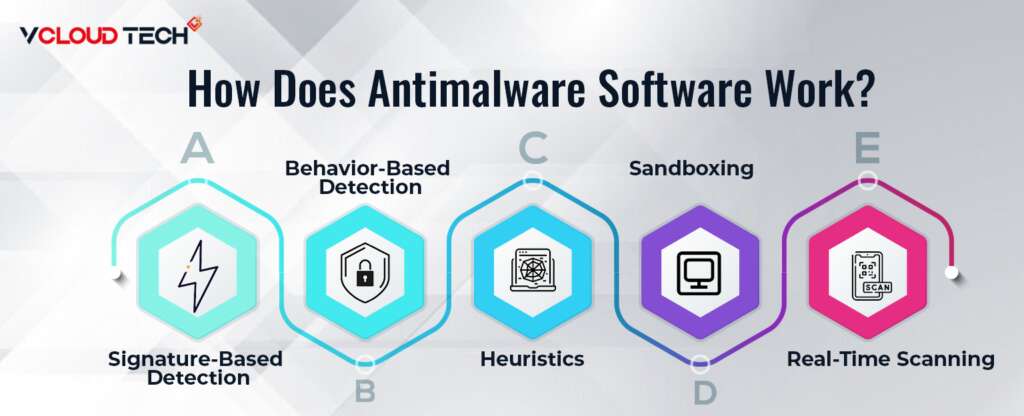
It combines techniques, including signature-based detection, behavior-based detection, and heuristics.
Signature-Based Detection:
Signature-based detection is one of the most common techniques antimalware software uses. It involves comparing files on a system to a database of known malware signatures. If a file matches a signature in the database, the antimalware software will flag it as malware and either quarantine or delete it.
Behavior-Based Detection:
Antimalware software uses behavior-based detection to identify malicious behavior that may not capture by traditional signature-based detection. It involves monitoring the behavior of programs on a system and looking for patterns that indicate malicious activity, such as attempts to modify system settings or access sensitive data.
Heuristics:
This is a technique used by antimalware software to Identify Potential Threats based on patterns in code. Heuristics involves analyzing the behavior of programs and looking for suspicious code patterns that may indicate the presence of malware.
Sandboxing:
It is a technique some antimalware software uses to isolate and test potentially malicious files in a safe environment. Sandboxing involves running a potentially malicious file in a virtual background separate from the host operating system. That allows the antimalware software to observe the behavior of the file and determine if it is malicious before allowing it to run on the host system.
Real-Time Scanning:
Real-time scanning is a feature of many antimalware software programs that monitors files and processes on a system in real time. That allows the antimalware software to detect and block malware as it attempts to execute on the system.
Malware Protection Best Practices
Malware is a persistent threat to the Security of Computer Systems and data. Protecting against malware requires a combination of technical controls, user awareness, and proactive security measures.

Here are some additional best practices for protecting against malware:
Implement a Security Awareness Program:
Educate employees on safe computing practices about Malware Protection, such as not opening unsolicited emails, avoiding downloading software from untrusted sources, and being cautious of social engineering attacks. Regular Training and Awareness Programs can help users identify and report potential security threats.
Use Multi-Factor Authentication:
Implement multi-factor authentication (MFA) for all systems and applications that contain sensitive data. That will provide Malware protection against unauthorized access to systems and data.
Use a Web Filter:
A web filter can help prevent users from accessing malicious websites or downloading potentially harmful files. Implement Web Security through Web filters can also block phishing emails and other social engineering attacks.
Disable Unnecessary Services and Protocols:
Disable any unnecessary services and protocols on your systems, including those unused. That can help reduce the attack surface and limit the potential for malware to exploit vulnerabilities in unneeded services.
Regularly Review and Update Security Policies:
Regularly review and update Network Security policies to ensure they reflect the latest security threats and best practices. Policies should cover all security aspects, including access control, data protection, and incident response.
Implement Least Privilege:
Implement the principle of least Privilege Management, which means giving users only the access they need to perform their job functions. That can help limit the impact of a malware infection by reducing the attack surface.
Use Application Allow Listing:
Application allows listing is a security technique that allows only trusted applications to run on a system. That can help prevent the execution of malware by blocking unauthorized applications.
Reach out to us and book a Free Consultation with vCloud Tech or chat with one of our representatives. Connect with us on Twitter, Facebook, Instagram, and LinkedIn for more information.