What is IIoT Security?
IIoT Security allows a network administrator and her OEM to secure and manage connected device endpoints on a network. IIoT devices are constantly transmitting important data. Using end-to-end encryption is essential to protect this data from hackers. Therefore, all IIoT devices should have encrypted data transfer capabilities, and this capability is always leveraged. The Industrial Internet of Things (IIoT) is the extension and use of the Internet of Things (IoT) in industrial sectors and applications. With his focus on Machine-to-Machine (M2M) communications, Big Data and Machine Learning, IIoT enables industries and Digital Enterprises to increase the efficiency and reliability of their operations. So Barracuda Secure Connector for IoT provides industries with Cybersecurity to protect their digital assets on their production floor that are just as much a target as your IT environment.
IIoT includes industrial applications such as robotics, medical devices, and software-defined manufacturing processes. The IIoT goes beyond the usual consumer and interconnected physical devices commonly associated with the industrial IoT. What sets it apart is the intersection of Information Technology (IT) and Operational Technology (OT). OT refers to the interactions between active processes and Industrial Control Systems (ICS), including Human-Machine Interfaces (HMIs), Supervisory Control and Data Acquisition systems (SCADA), Distributed Control Systems (DCS), and Programmable Logic Controllers (PLCs).
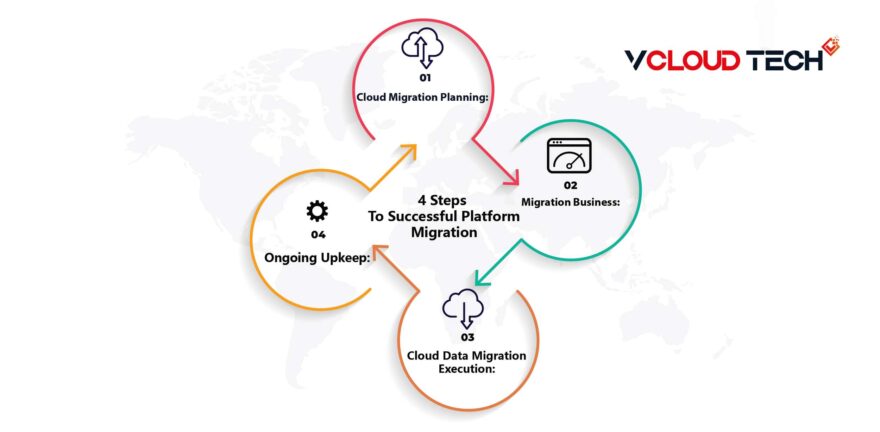
How it works: IIoT Technology
For an IIoT network to be effective, it must do two crucial things: connect devices and assets to each other and connect them to a central system. We also store, manage, analyze and enable the effective use of the data we collect and transmit. IIoT Security networks rely on the following technologies:
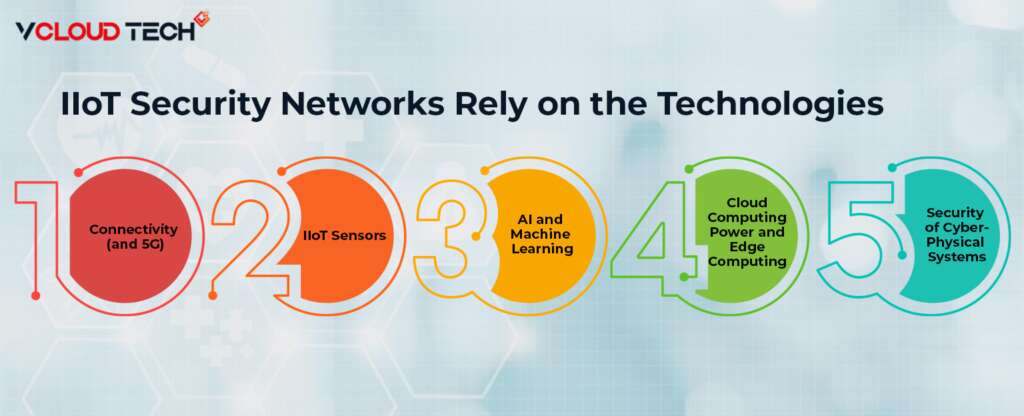
Connectivity (5G):
IIoT networks need the capacity to send and receive massive amounts of data generated by machines and devices. That has traditionally been enabled and limited by the power of Wi-Fi connectivity. But 5G and other advances in cellular networks are changing this formula, increasing bandwidth to handle large amounts of data, and reducing latency and power consumption.
IIoT Sensors:
Now sensors typically installed in new factories and machines. However, analogue equipment and production plants can also equipped with IoT gateway devices such as cameras and measuring equipment. That allows IIoT assets to detect environmental conditions, such as the proximity of other objects, air pressure and humidity, engine speed, liquid level, and different mechanical needs.
Cloud Computing Power and Edge Computing:
Both Cloud Computing and edge computing technologies have significantly increased the flexibility and ease of use of the IIoT. Through the cloud, IIoT networks can use high computing power and storage capacity as needed. That means devices in your network can collect and transmit larger and more complex data sets. Edge computing means taking a system that can process and analyze that data and making it on-premises (physically close to the IIoT network).
AI and Machine Learning:
Artificial intelligence and machine learning technologies enable companies to process their IIoT data using advanced predictive analytics. Extreme Defender for IoT secures your organization’s critical IoT devices by applying and enforcing device profiles that control your IoT device network access. Modern databases and machine learning algorithms also help companies manage and understand diverse data sets and complex unstructured data. These tools are used to analyze IIoT data in almost limitless combinations with other data insights, such as customer feedback, weather forecasts, marketing analytics, and more.
Security of Cyber-Physical Systems:
The same connectivity that breathes life into IIoT networks also puts them at risk. Most organizations have strict security and access protocols surrounding their core systems and databases, but IoT devices can be relatively vulnerable. Essentially, they act as basement windows, allowing full access to a reasonably secure system via traditional access points. Fortunately, security protocols and technologies have kept mainly pace with IIoT advancements.
What are some Common Threats to IIoT Security?
- Device Hijacking: If endpoints or sensors are compromised, so they may be under the control of malicious actors.
- Data Siphoning: Attackers can “eavesdrop” on your network traffic and gain access to personal and proprietary data.
- DDoS Attacks: Amazon, GitHub and Bank of America are a few significant companies hit by distributed denial of service attacks. These increasingly common attacks can cripple services across an enterprise.
- Spoofing: If an attacker gets between a centralized network and an unsecured endpoint, they can send fraudulent information that appears to come from the endpoint.
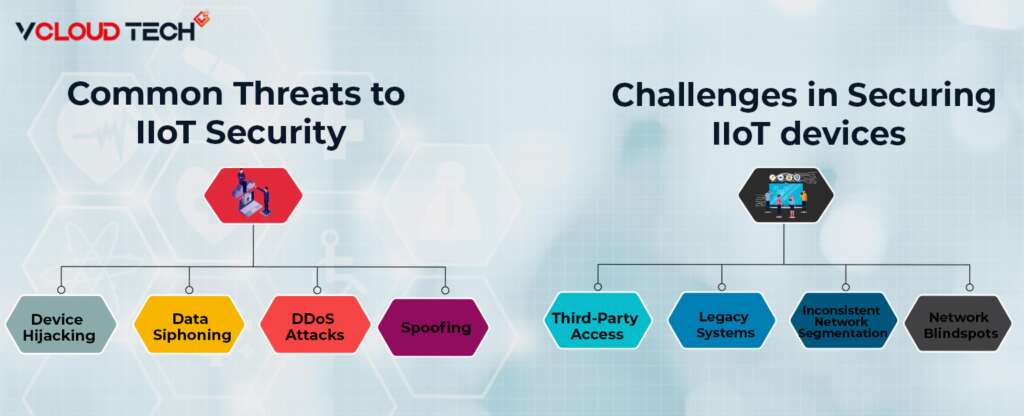
What are the Challenges in Securing IIoT devices?
- Third-Party Access: Giving technicians and contractors broad access to your network increases risk and also makes it challenging to manage effectively.
- Legacy Systems: Systems become an Industrial IoT Security risk when they can no longer patched or updated to protect against vulnerabilities.
- Inconsistent Network Segmentation: Limited and malicious lateral movement strategies often applied inconsistently across the various social networks today.
- Network Blind Spots: With the rapid growth and diversification of IoT devices and systems, network monitoring and control is becoming a complex task.
How can Network Administrators Secure their Networks and Devices Today?
IIoT security can be challenging, but we help professionals get up and running quickly and efficiently. For example, Check Point Quantum IoT Protect design to secure your networks and devices that use the Internet of Things (IoT) devices across Healthcare, enterprises, and Industrial Applications to deliver productivity advantages and also protect your systems from new Cyber-threats.
Legacy Device Protection:
Safely extend the life of IT Hyperconverged Infrastructure running legacy applications and unsupported operating systems that cannot retired.
Simplify and Centralize Remote Access:
Pre-connect air-gapped devices to the network for more efficient, secure remote maintenance and monitoring.
Efficient Incident Response:
Upon detection of malicious traffic, a kill switch can deploy to immediately stop all traffic destined for a specific micro-segment without impacting underlying device operations.
The Immediate Return on Investment:
Easy deployment without changing existing network configurations or exposing internal devices to the Internet.
Reduced Attack Surface:
Unpatched legacy connected devices are not exposed to insider threats such as lateral movement and ransomware.
Reduced Field Service Time:
Reduced on-site technician travel for service and maintenance, saving operating costs.
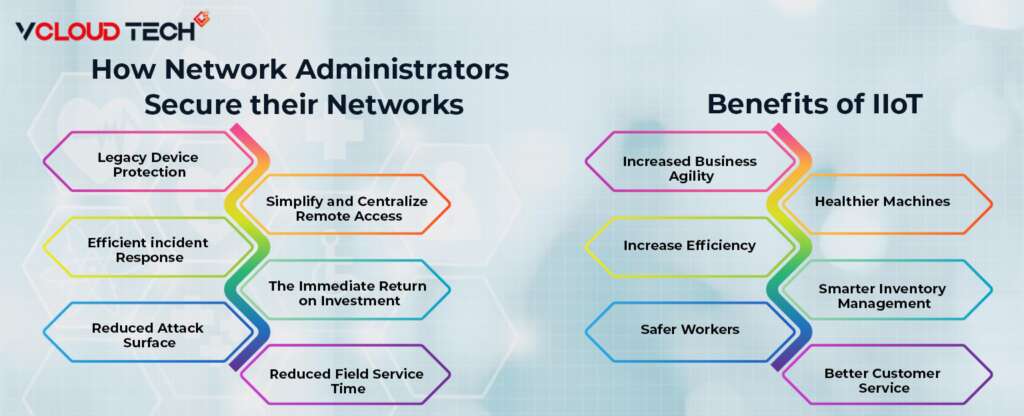
Benefits of IIoT and Cyber-Physical Systems
As part of the digital transformation process, IIoT networks provide potent tools for greater resilience and competitiveness.
Increased Business Agility:
When IIoT devices exchange data in real-time, they contribute to information networks that continuously collect, analyze, and learn from data. That enables companies to respond quickly and decisively to opportunities and risks. These same devices can also send data and receive instructions based on data analysis to adjust and Optimize Automated Workflows.
Healthier Machines:
Desktop Virtualization devices and machines in IoT networks continuously send operational logs and performance data. Then AI and machine learning algorithms can use this sensor data to gain valuable insight into forecasting and other maintenance needs, which can lead to significant cost savings.
Increase Efficiency:
Unfortunately, the attitude companies often adopt when prioritizing their operational needs is often “if it’s not broken.” This attitude can lead to legacy processes that are past their prime and hence need to be more efficient. Applying advanced analytics to his IIoT data yields ongoing recommendations and strategies to update procedures, streamline workflows, and improve efficiency and productivity.
Smarter Inventory Management:
At the present time customers want next-day delivery and ever-increasing variety and customization. So that means more extensive network of smaller, more distributed warehouses and a more expansive inventory containing more individual items. It helps connect everything in your supply network and lets your supply chain managers (and your customers) know where your list is at all times in real time.
Safer Workers:
In any industrial environment, there is always the risk of injury or overwork. So many companies are using their IoT occupational safety equipment to mitigate this risk. These can provide alerts via wearable sensors or use VR headsets to help employees combine sensory experiences with the precision of intelligent devices and machines.
Better Customer Service:
IIoT networks connect devices and machines within an organization and hence integrate customer experience and input. This integration will enable a more seamless shopping experience, more transparent and personalized logistics, and a more extraordinary ability to incorporate customer feedback and preferences into the manufacturing and development of new products.
Reach out to us and book a Free Consultation with vCloud Tech or chat with one of our representatives. Connect with us on Twitter, Facebook, Instagram, and LinkedIn for more information.