What is an Intrusion Prevention System?
An intrusion prevention system (IPS) is a hardware or software-based network security technology that continuously scans your network for harmful activity and takes steps to stop it from happening by reporting, blocking, or eliminating it when it does. That is more sophisticated than malware detection (IDS), which can only alert administrators when it discovers suspicious activity. A Next Generation Firewall (NGFW) or Universal Threats Administration (UTM) solution may include an intrusion prevention system. However, it must have sufficient power to scan substantial traffic without degrading network performance, as with several network security methods.
How does an Intrusion Prevention System work?
Inline Network Intrusion Prevention Systems are frequently placed directly behind a firewall in the network traffic path between a source and a destination. Intrusion prevention systems can detect threats in several ways.
Signature-based:
This method assesses activities about recognized threat signatures. The limitation of this approach is that it will only detect and block known assaults.
Anomaly-based:
This approach tracks unusual behavior by contrasting a representative sample of network connections with a reference point. Although it is more reliable than signature-based monitoring, it could also result in false positives. Machine learning-based Intrusion Prevention Solutions that are powerful and currently support anomaly-based monitoring.
Policy-based:
This technique is frequently less used than a signature- or anomaly-based monitoring. Enforce the security guidelines established by the company, and stop acts that go against them. Administrators must configure security policies to accomplish that.
The IPS can do various automated tasks when it discovers malicious activity, including alerting administrators, discarding packets, restricting traffic from source addresses, and reconnecting connections. Additionally, some intrusion detection systems use honeypots or entice high-value data to draw attackers and thwart their objectives.
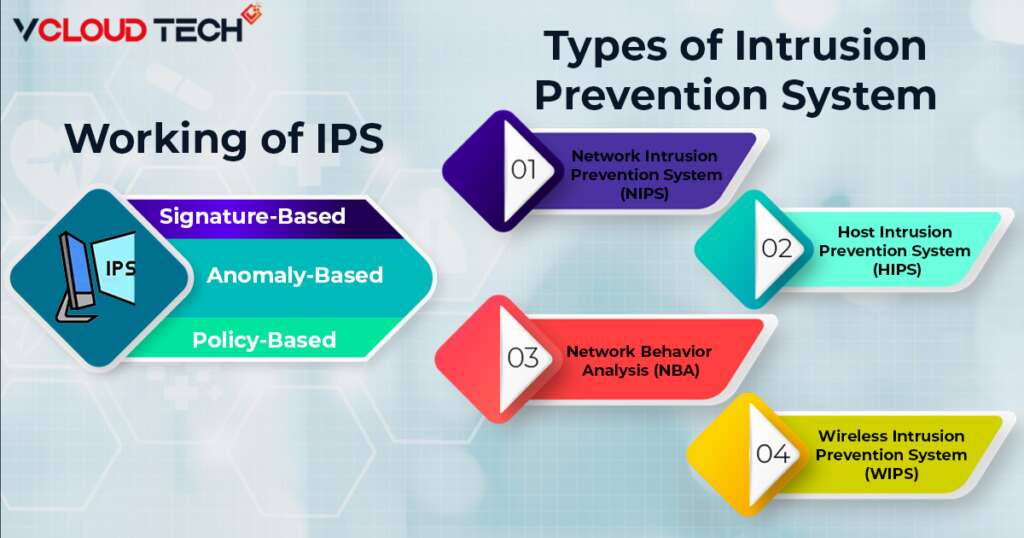
Types of Intrusion Prevention Systems
There are several types of IPS, each with the slightest difference in objective:
Network Intrusion Prevention System (NIPS):
This type of IPS is installed only in strategic areas, where it can monitor all network traffic and proactively look for threats.
Host Intrusion Prevention System (HIPS):
In contrast to NIPS, a HIPS is placed on an endpoint (such as a PC) and only keeps track of inbound and outbound traffic from that particular device. Since it serves as the last line of defense for attacks that have moved past the NIPS, it works best in conjunction with one.
Network Behavior Analysis (NBA):
NBA analyzes network traffic to spot unusual traffic conditions, such as DDoS (Distributed Denial of Service) attacks.
Wireless Intrusion Prevention System (WIPS):
If a wireless Trend Micro Intrusion Prevention System (WIPS) identifies unwelcome devices on a Wi-Fi network, it removes undesirable devices from the web.
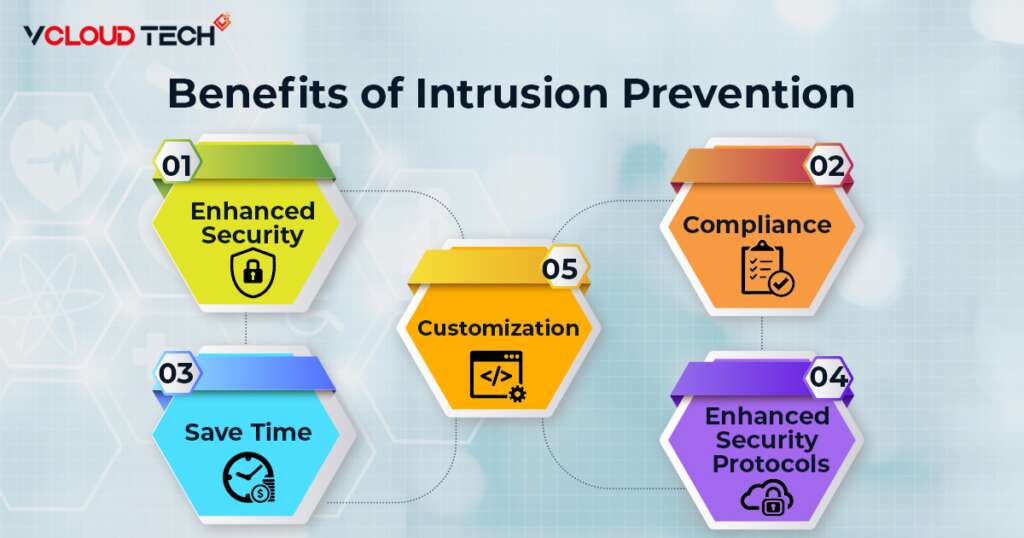
What are the benefits of an Intrusion Prevention System?
Numerous advantages of IPS include:
Enhanced Security:
IPS collaborates with other security tools to identify threats that different mechanisms cannot. For systems that employ anomaly-based detection, this is especially true. Superior application security also provides by advanced application awareness.
Enhanced Effectiveness of other Security Protocols:
Extreme AirDefense IPS filter out harmful traffic before it reaches management and other security devices, lowering their workload and improving their effectiveness.
Save Time:
Since IPS are primarily automated, your IT personnel will have less work to do.
Compliance:
IPS satisfies several compliance standards established by PCI DSS, HIPAA, etc. Additionally, it offers valuable test results.
Customization:
Organizations utilizing IPS can build up their IPS with custom security policies to give unique security controls.
Why Are Intrusion Prevention Systems Important?
For several reasons, Fortinet FortiGuard IPS is a crucial component of a corporate security system. First, modern networks carry a lot of traffic and have several entry points, making monitoring and response impossible. The risks to enterprise system security are also: More and more sophisticated (this is particularly true for Cloud Security, where a highly networked environment can widen your attack vector and increase your susceptibility to threats). In this situation, the automated features of an IPS are crucial because they let enterprises respond to attacks rapidly without taxing their IT staff. IPS is a vital component of an organization’s security infrastructure and an essential tool in preventing even the most severe and complex attacks.
An IPS is used to spot malicious behavior, register threats found, report threats found, and take preventive measures to stop threats from hurting you. IPS tools Monitor your Network in real-time constantly. IPS Systems and security managers can employ intrusion prevention as a threat detection technique in security environments. These tools assist the system in preparing for potential eventualities. Furthermore, suspicious activity might appear in various ways, making a plan necessary to spot future attacks. IPS develop to enhance intrusion detection systems’ fundamental capabilities (IDS).
Reach out to us and book a Free Consultation with vCloud Tech or chat with one of our representatives. Connect with us on Twitter, Facebook, Instagram, and LinkedIn for more information.








