In cybersecurity’s vast and interconnected realm, threats come in various shapes and sizes. One of the most notorious and deceptive is the Trojan horse virus. Named after the ancient Greek tale of the wooden horse used to infiltrate the city of Troy, a Trojan horse virus employs similar tactics in the digital world. This blog will delve into the depths of Trojan horse viruses, exploring what they are, how they operate, and what steps you can take to protect your digital world from these cunning cyber adversaries.
What Is a Trojan Horse Virus?
A Trojan Horse Virus is malicious software infiltrating a computer by masquerading as a legitimate program. The common approach involves cybercriminals employing social engineering tactics to embed harmful code within authentic software, aiming to obtain access to users’ systems through their software illicitly. A concise explanation of a Trojan is that it is a type of malware often concealed as an attachment in an email or a downloadable file offered for free. Once it infiltrates the user’s device, the evil code proceeds to carry out the specific tasks devised by the attacker, which may involve gaining unauthorized access to corporate systems, monitoring users’ online activities, or stealing sensitive data. Signs of a Trojan’s presence on a device include unusual occurrences like unexpected alterations to computer settings.
History of the Trojan Horse
The original tale of the Trojan horse can be found in the Aeneid by Virgil and the Odyssey by Homer. According to this narrative, the adversaries of the city of Troy devised a cunning scheme to breach the city’s defenses. They presented a large wooden horse as a deceptive gift, concealing soldiers inside its hollow belly. Once this deceptive gift was admitted through the city gates, the hidden soldiers emerged and facilitated the entry of their comrades, ultimately leading to the fall of Troy. Several aspects of this story aptly justify the term “Trojan horse” when referring to cyber-attacks of this nature:
- The Trojan Horse offered them a novel and effective means of gaining access they had sought for an extended period. Similarly, a Trojan virus can be an innovative way to breach otherwise robust defenses, bypassing security measures.
- The Trojan horse in the tale assumed the guise of a genuine gift, concealing its true intent. Analogously, a Trojan virus disguises itself as legitimate software, luring users into unwittingly accepting it.
- Within the Trojan Horse, the infiltrating soldiers took command of the city’s defense system. Similarly, once inside a computer, a Trojan virus can seize control, potentially rendering the system vulnerable to other malicious intruders.
These parallels underscore why “Trojan horse” is fitting when describing cyber attacks that employ deception and fraud to compromise digital security. Check Point Cloud Guard’s public cloud security provides the same level of protection, that protects the customer’s premises-based Networks Cloud in an application designed for flexible and dynamic characteristics of the cloud.
How Do Trojan Horse Viruses Spread?
Trojans use various cunning methods to infiltrate systems, often relying on the unwitting actions of users. Here are some common distribution techniques employed by Trojan horse viruses:
- Email Attachments: Cybercriminals send malicious attachments in seemingly innocent emails. Once the user downloads and opens the extension, the Trojan is unleashed.
- Drive-by Downloads: Visiting compromised or malicious websites can lead to the automatic download and execution of Trojans without any user interaction.
- Infected Software: Trojans can be bundled with pirated or counterfeit software, enticing users to download and install them.
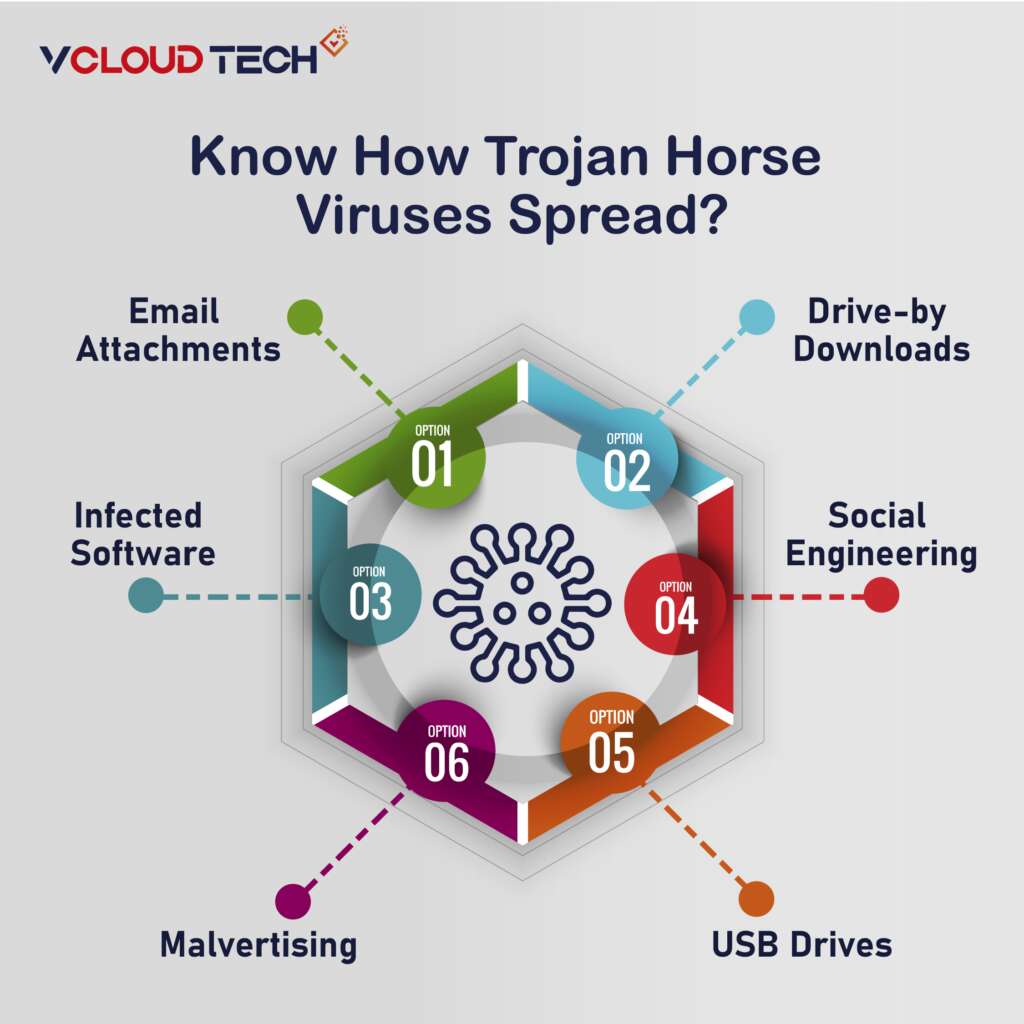
- Social Engineering: Cybercriminals may trick users into downloading Trojans by posing as legitimate entities, such as tech support or trustworthy organizations.
- Malvertising: Malicious advertisements can lead users to compromised websites or trigger drive-by downloads when clicked.
- USB Drives: Trojans can spread via infected USB drives or other removable media when users unknowingly connect them to their systems.
How Do Trojans Work?
In contrast to computer viruses, a Trojan horse cannot independently manifest itself; it relies on a user to download the server-side component of the application to become operational. That necessitates the implementation of an executable (.exe) file and installing the program for the Trojan to initiate an attack on a device’s system.
Trojan viruses propagate through seemingly legitimate emails and email attachments distributed in masse to reach as many recipients as possible. When a recipient opens such an email and downloads the malevolent attachment which will effect your Email Security, the Trojan server is installed and automatically runs each time the compromised device is powered on.
Devices can also fall victim to Trojans through social engineering tactics employed by cybercriminals to manipulate users into downloading malicious applications. These harmful files might be concealed within banner advertisements, pop-up ads, or website links.
Furthermore, a computer contaminated by Trojan malware can spread the infection to other computers. Cybercriminals effectively transform the device into a “zombie computer,” granting them remote control without the user’s awareness. Subsequently, hackers can employ the zombie computer to disseminate malware throughout a network of devices called a botnet.
For instance, a user may receive an email from a familiar source, complete with a legitimate attachment. However, unbeknownst to the user, this attachment contains malicious code that executes and installs the Trojan on their device. Often, the user remains oblivious to any irregularities as their computer continues to operate normally, displaying no indications of infection.
Protection and Prevention
The malware remains dormant until the user takes a specific action, such as visiting a particular website or using a banking application. That prompts activating the malicious code, enabling the Trojan to execute the hacker’s intended actions. Depending on the Trojan’s type and construction, the malware may either delete itself, return to a dormant state, or persistently remain active on the device.
It’s important to note that Trojans can also target and infect smartphones and tablets using variants of mobile malware. That may occur through attackers redirecting traffic to a device connected to a Wi-Fi network and subsequently using it to launch cyberattacks.
Most Common Types of Trojan Malware
Cybercriminals employ a wide array of Trojan horse viruses to execute various actions and diverse attack strategies. Among the most prevalent types of Trojans utilized are:
Backdoor Trojan:
This type of Trojan enables attackers to establish remote access to a computer, providing them with control via a concealed entry point. This control allows the malicious actor to carry out various actions on the compromised device, including file deletion, system reboots, data theft, or the introduction of additional malware. Backdoor Trojans are often instrumental in forming botnets through a network of compromised computers.
Banker Trojan:
Designed to specifically target users’ financial information and banking accounts, a banker Trojan endeavors to steal data related to credit and debit cards, electronic payment systems, and online banking services.
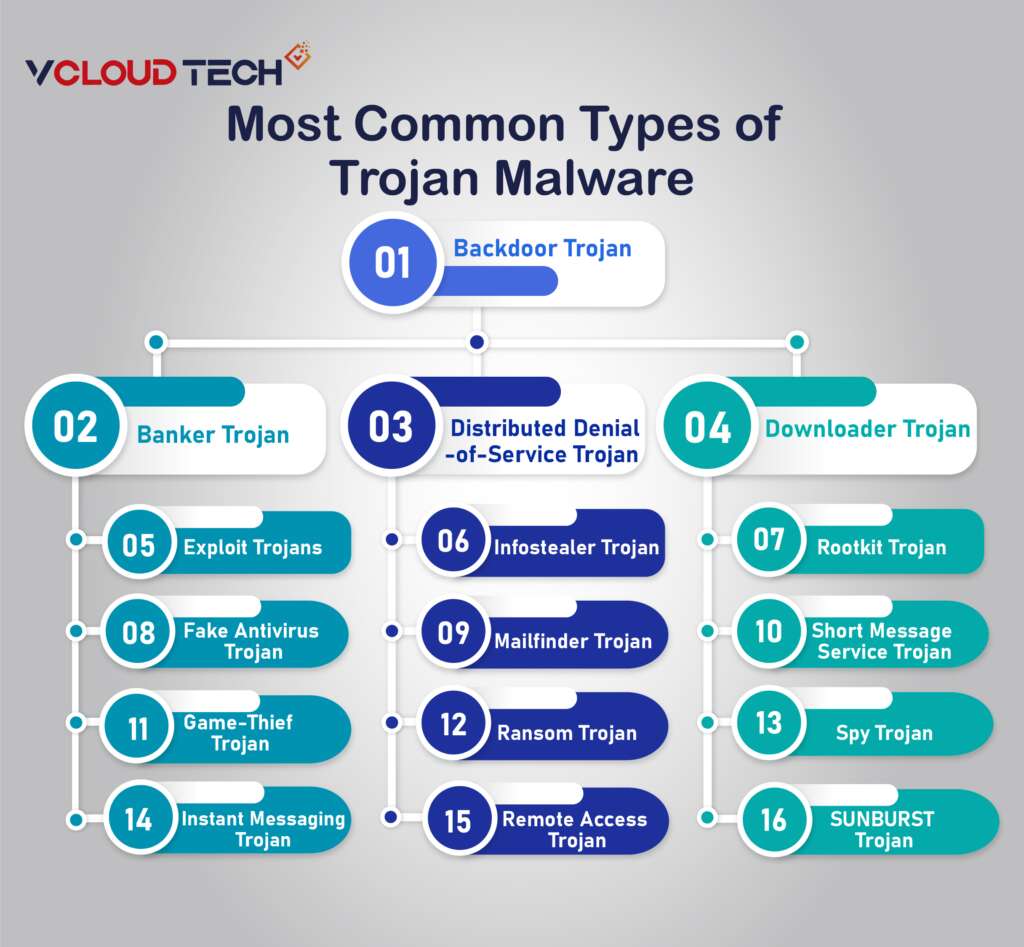
Distributed Denial-of-Service (DDoS) Trojan:
These Trojans orchestrate attacks aimed at overwhelming a network with excessive traffic. By sending numerous requests from a single computer or a group of computers, these Trojans aim to saturate a target web address, leading to a denial of service.
Downloader Trojan:
A downloader Trojan focuses on infecting computers already compromised by malware, subsequently downloading and installing additional malicious programs. These could include more Trojans or other types of malware like adware.
Exploit Trojans:
Exploit Trojans contain code or data that capitalizes on specific vulnerabilities within applications or computer systems. Cybercriminals target users through phishing attacks and then leverage the code within the program to exploit known weaknesses.
Fake Antivirus Trojan:
Fake antivirus Trojans mimic the actions of legitimate antivirus software. They are designed to detect and purportedly remove threats, much like a genuine antivirus program, and then coerce users into paying to remove potentially non-existent threats.
Game-Thief Trojan:
Specifically crafted to steal user account information from individuals engaged in online gaming.
Instant Messaging (IM) Trojan:
IM Trojans exploit messaging services to pilfer users’ login credentials and passwords, often focusing on popular messaging platforms like AOL Instant Messenger, ICQ, MSN Messenger, Skype, and Yahoo Pager. Implementing Passwordless Authentication Solutions can mitigate the risks associated with credential theft by eliminating the need for user generated passwords. Solutions such as biometric authentication or one-time passcodes(OPT) Multi Factor authentication (MFA) sent via secure channels provide a more robust and secure way to verify user identity.
Infostealer Trojan:
Infostealer Trojans can either install other Trojans or conceal the presence of malicious programs, making it challenging for antivirus systems to detect them during scans.
Mailfinder Trojan:
This Trojan aims to harvest and steal email addresses stored on a computer.
Ransom Trojan:
Ransom Trojans seek to disrupt a computer’s functionality or lock access to data, demanding a ransom fee from the user or organization to reverse the damage or unlock the affected data.
Remote Access Trojan:
Like a backdoor Trojan, this malware provides attackers complete control over a user’s computer, facilitated through a remote network connection. This access is used for information theft or surveillance.
Rootkit Trojan:
Rootkits are malware that hides on a user’s computer to evade detection, enabling others to persist on an infected computer for extended periods.
Short Message Service (SMS) Trojan:
These Trojans infect mobile devices and can send and intercept text messages, including sending letters to premium-rate phone numbers, resulting in increased costs on a user’s phone bill.
Spy Trojan:
Designed to observe a user’s activity on their computer clandestinely, Spy Trojans log keystrokes, capture screenshots, access applications used, and track login credentials.
SUNBURST Trojan:
The SUNBURST Trojan virus targeted numerous SolarWinds Orion Platform victims. It infiltrated systems through a trojanized version of a legitimate SolarWinds digitally signed file, SolarWinds.Orion.Core.BusinessLayer.dll. This trojanized file acted as a backdoor, remaining dormant for a period before retrieving commands to transfer, execute, conduct surveillance, reboot, and halt system services, communicating over HTTP to predetermined URIs.
How To Recognize a Trojan Virus?
A Trojan horse virus can frequently linger undetected on a device for an extended period while escaping the user’s notice regarding their computer’s infection. Nevertheless, indications that may signal the existence of a Trojan encompass unexpected alterations in computer configurations, a decline in computer performance, or the occurrence of unusual activities. To identify a Trojan, the most effective approach is to search for the device utilizing a Trojan scanner or malware-removal software.
Examples of Trojan Horse Virus Attacks
Trojan attacks have had a significant impact by causing substantial damage through computer infections and the theft of user data. Notable examples of Trojans include:
- Rakhni Trojan: The Rakhni Trojan is responsible for distributing either ransomware or a cryptojacking tool, allowing attackers to hijack a device’s resources for cryptocurrency mining. This infection method compromises devices and can result in financial losses.
- Tiny Banker: Tiny Banker is a Trojan that facilitates the theft of users’ financial information. It gained attention after infecting at least 20 U.S. banks, highlighting its capacity to compromise the security of financial institutions and their clients.
- Zeus or Zbot: Zeus is a versatile toolkit utilized by cybercriminals to target financial services. It empowers hackers to create their customized Trojan malware. The source code of Zeus incorporates techniques such as form grabbing and keystroke logging, enabling it to pilfer user credentials and financial data, posing a substantial threat to the security of financial institutions and individuals alike.
How To Protect Yourself from Trojan Viruses?
A Trojan horse virus can persist undetected on a device for an extended period. Often evading the user’s awareness of their computer’s compromise. Nevertheless, there are distinctive indicators that may suggest the presence of a Trojan. Such as abrupt alterations in computer settings, a degradation in computer performance, or unusual activities. The most effective method for identifying a Trojan is to conduct a comprehensive scan of the device using specialized tools. Such as a Trojan scanner or malware-removal software. Here are some crucial steps you can take to protect your digital world:

- Use Reliable Security Software: Invest in reputable antivirus and anti-malware software and keep it current. These programs can help detect and remove Trojans before they cause harm.
- Regularly Update Your Operating System and Software: Ensure your operating system, web browsers, and all installed software are updated with the latest security patches. Cybercriminals often exploit vulnerabilities in outdated software.
- Exercise Caution with Email: Be wary of email attachments and links. Especially from unknown senders. Avoid downloading attachments or clicking on links if you’re not expecting them.
- Stay Informed: Educate yourself and your employees or family about the latest cybersecurity threats and best practices. Awareness can go a long way in preventing infections.
Download Software from Trusted Sources:
Only download software from official websites or reputable app stores. Avoid pirated or cracked software, as it often contains hidden Trojans.
- Use a Firewall: Enable and configure a firewall on your computer to monitor incoming and outgoing traffic. Firewalls can block suspicious connections and provide an additional layer of protection.
- Regular Backups: Maintain regular Data backups of your important files on offline or cloud storage. That can help you recover your data in case of a Trojan infection or other data loss events.
- Network Security: Implement strong network security measures, including using strong, unique passwords, encryption, and network segmentation to limit the impact of a Trojan infection.
Conclusion
Trojan horse viruses are cunning and versatile threats that can cause significant damage to individuals and organizations alike. By understanding how these digital deceptions operate and implementing robust cybersecurity practices. You can greatly reduce the risk of falling victim to them. Remember that cybersecurity is an ongoing process. Staying vigilant is key to protecting your digital assets in an ever-evolving threat landscape.
Reach out to us and book a Free Consultation with vCloud Tech or chat with one of our representatives. Connect with us on Twitter, Facebook, Instagram, and LinkedIn for more information.









