Preventing phishing has become crucial as many cybercriminals resort to online scams to steal personal information. While we’ve become adept at avoiding spam emails, phishing emails can appear remarkably convincing, with some tailored specifically for you. Given the likelihood of encountering a phishing attempt at some point, it’s essential to be aware of the warning signs, as identifying phishing can be more challenging than it seems.
Across the internet, phishing attacks have lured unsuspecting individuals into divulging sensitive information such as bank details and social security numbers. Moreover, cybercriminals have become increasingly adept at concealing their true intentions. These scams sometimes hide behind familiar and trusted sources, such as colleagues, financial institutions, or government agencies. Simply clicking on a link could make you the next target of the scammer.
What is Phishing?
Preventing phishing has become crucial as many cybercriminals resort to online scams to steal personal information. While we’ve become adept at avoiding Spam Emails, phishing emails can appear remarkably convincing, with some tailored specifically for you. Given the likelihood of encountering a phishing attempt at some point, it’s essential to be aware of the warning signs, as identifying phishing can be more challenging than it seems.
Across the internet, phishing attacks have lured unsuspecting individuals into divulging sensitive information such as bank details and social security numbers. Moreover, cybercriminals have become increasingly adept at concealing their true intentions. These scams sometimes hide behind familiar and trusted sources, such as colleagues, financial institutions, or government agencies. Simply clicking on a link could make you the next target of the scammer.
Types of phishing
Phishing is a cyber-attack where malicious actors attempt to deceive individuals into revealing sensitive information, such as passwords, credit card numbers, or personal data. There are several Phishing Attacks, each with its tactics and objectives. Here are some common types of phishing:
Email Phishing:
This is the most common type of phishing. Attackers send deceptive emails that appear to come from a trusted source, such as a bank, social media platform, or government agency. These emails often contain links to fake websites that steal login credentials or install Malware.
Spear Phishing:
Spear phishing is a targeted form of phishing. Attackers customize their messages for specific individuals or organizations, often using information from social media or other sources to make the emails seem more convincing.

Vishing (Voice Phishing):
Vishing involves phone calls instead of emails. Attackers impersonate legitimate organizations or individuals over the phone, attempting to extract sensitive information or money from the victim.
Smishing (SMS Phishing):
Smishing attacks use text messages to trick individuals into clicking on malicious links or responding with personal information. These messages may come from a trusted source or may claim that the recipient has won a prize.
Pharming:
Pharming involves redirecting website traffic to fraudulent sites without the user’s knowledge. Attackers compromise DNS servers or manipulate host files to achieve this. Victims are led to believe they are on a legitimate website when, in fact, they are on a fake one.
Clone Phishing:
In clone phishing, attackers create a nearly identical copy of a legitimate email that the victim has previously received and may have already acted upon. The cloned email contains a malicious link or attachment.
Whaling:
Whaling is phishing targeting high-profile individuals or senior executives within an organization. Attackers aim to trick these individuals into divulging sensitive corporate information or credentials.
Ransomware Phishing:
This type of phishing includes emails or messages containing malicious attachments or links that, when clicked, can lead to the installation of ransomware on the victim’s system. Ransomware encrypts the victim’s files and demands a ransom for decryption.
How Phishing Works?
Email Phishing is a form of social engineering and cybersecurity attack in which the perpetrator impersonates someone else through various electronic communication methods, including email, social networks, and SMS text messages, to obtain sensitive information.
Phishers often utilize publicly available sources of information, like LinkedIn, Facebook, and Twitter, to gather details about their potential victims, such as their personal information, professional background, interests, and activities. This information is frequently used to craft convincing phishing emails, including details like names, job titles, and email addresses.
Typically, a targeted individual will receive a message that appears to originate from a familiar contact or reputable organization. The attack is executed when the victim clicks on a malicious file attachment or follows a hyperlink leading to a malicious website. In both scenarios, the attacker aims to install malware on the victim’s device or redirect them to a fraudulent website. These fake websites are designed to deceive victims into disclosing personal and financial information, including passwords, account IDs, or credit card details.
How Do You Recognize a Phishing Email?
Phishing messages that successfully deceive recipients are often challenging to differentiate from legitimate statements. They frequently appear to originate from reputable companies, complete with corporate logos and other identifying information. Nonetheless, several indicators can suggest a letter is an Email Phishing attempt. These indicators include:
- The message contains subdomains or URLs that appear suspicious, include misspellings, or employ typosquatting tactics.
- The recipient’s email address is public, like Gmail, rather than a corporate one.
- The message is designed to elicit the recipient’s fear or sense of urgency.
- The message includes a request for personal information verification, such as financial details or a password.
- The message needs to be better written, containing spelling or grammatical errors.
Phishing Techniques
Phishing attacks go beyond simply sending emails and hoping for recipients to click on malicious links or open harmful attachments. Attackers employ various techniques to trap their victims, including:
URL Spoofing:
Attackers use JavaScript to overlay a legitimate URL over a browser’s address bar, only revealing the URL when hovering over an embedded link or using JavaScript to change it.
Link Manipulation:
Also known as URL hiding, this technique involves creating a malicious URL that appears to link to a legitimate site or webpage. Still, it leads to a malicious web resource.
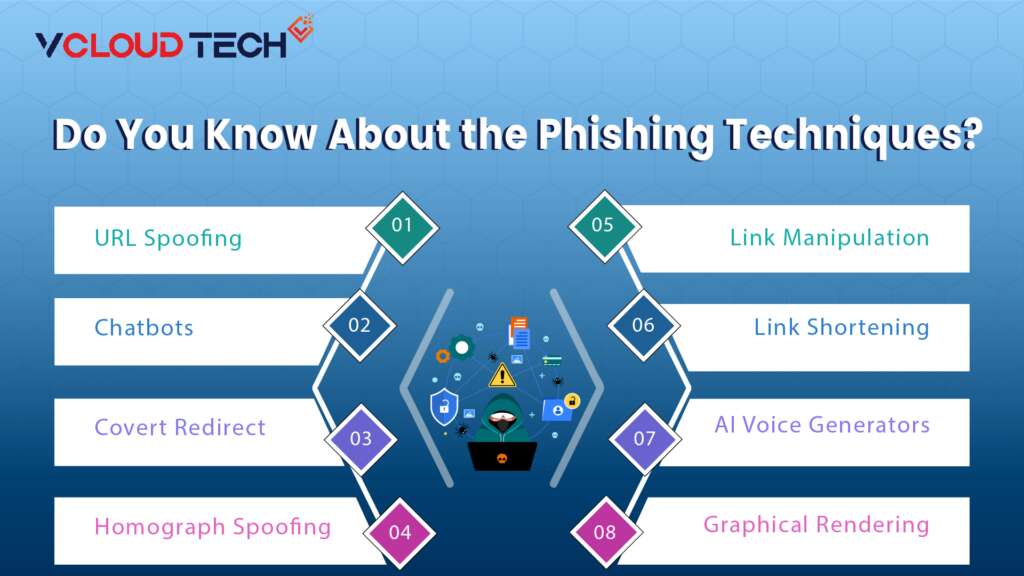
Link Shortening:
Attackers use link shortening services like Bitly to obscure the destination of a link, making it difficult for victims to determine if it leads to a legitimate or malicious website.
Homograph Spoofing:
Attackers register domains that use characters closely resembling trusted domain names, making them appear legitimate at first glance.
Graphical Rendering:
Rendering a message as a graphical image can bypass phishing defenses that scan emails for common phishing terms or phrases.
Covert Redirect:
Victims are redirected to a seemingly trusted source that requests authorization to connect to another website. However, the redirected URL is an intermediate, malicious page that solicits authentication information before forwarding the victim to the legitimate site.
Chatbots:
Attackers employ AI-enabled chatbots to eliminate common grammatical and spelling errors found in phishing emails, making the messages appear more complex and genuine, thus harder to detect.
AI Voice Generators:
Attackers use AI voice generator tools to mimic personal authorities or family members during phone calls, enhancing the personalization of phishing attempts and increasing their chances of success. Attackers only require a small audio sample of the victim’s manager or family member to achieve this.
How To Prevent Phishing?
To enhance protection against phishing messages and prevent them from reaching end users, experts recommend implementing a layered approach using the following security tools and practices:
1. Antivirus software.
2. Desktop and network firewalls.
3. Anti-spyware software.
4. Anti-phishing toolbars installed in web browsers.
5. Gateway email filters.
6. Web Security gateways.
7. Spam filters.
8. Phishing filters provided by vendors like Microsoft.
For enhanced Email Security, enterprise mail servers should employ at least one email authentication standard to verify the authenticity of inbound emails. Examples include the DomainKeys Identified Mail (DKIM) protocol, which allows users to block all messages except those cryptographically signed, and the Domain-based Message Authentication, Reporting, and Conformance (DMARC) protocol, which provides a framework for better blocking of unsolicited emails.
Numerous online resources are available to assist in combating phishing attacks. Organizations can turn to resources such as the Anti-phishing Working Group Inc. and the federal government’s OnGuardOnline.gov website for guidance on recognizing, avoiding, and reporting phishing attacks. Interactive security Phishing Awareness training tools can be valuable for educating employees about phishing techniques and how to identify them. Employees should be properly informed about the risks of clicking links, opening attachments, or engaging with suspicious emails from unknown sources.
How To Stop Phishing Emails?
Stopping phishing emails requires a combination of vigilance, technology, and best practices. Here are some steps you can take to help prevent and Stop Phishing Emails:
Use Email Filters:
- Enable and regularly update your email provider’s spam filters to enhance email security. They often have built-in mechanisms to detect and filter out phishing emails.
Look for Red Flags:
- Be cautious of emails from unknown senders or those with suspicious or generic subject lines.
- Check for misspelled words, poor grammar, and unusual email addresses or domains.
Verify the Sender:
- Hover over email addresses or sender names to see the full email address. Be wary of email addresses that look slightly off or unfamiliar.
- If an email claims to be from a reputable organization, verify the sender’s legitimacy by contacting them through their official website or phone number.

Avoid Clicking Links:
- Do not click on links or download attachments from suspicious or unexpected emails.
- Hover over links to preview the URL, but do not click unless you know it is safe.
Watch for Urgency and Threats:
- Be cautious of emails that create a sense of urgency or threaten consequences if you don’t take immediate action.
- Phishers often use fear tactics to trick recipients into providing sensitive information.
Enable Two-Factor Authentication (2FA):
- Enable 2FA for your email accounts. That adds an extra layer of security, making it harder for attackers to gain access.
Educate Yourself and Your Team:
- Stay informed about the latest Phishing Techniques and share this knowledge with colleagues and family.
- Train employees and team members to recognize and report phishing attempts in a corporate setting.
Report Phishing Emails:
- If you receive a phishing email, report it to your email provider or IT department. They can take action to block similar emails.
Use Anti-phishing Tools:
- Consider using browser extensions or software that offer anti-phishing protection. These tools can help identify and block phishing websites.
Keep Software Updated:
- Ensure your operating system, web browser, and security software are current. Updates often include patches for security vulnerabilities.
Reach out to us and book a Free Consultation with vCloud Tech or chat with one of our representatives. Connect with us on Twitter, Facebook, Instagram, and LinkedIn for more information.









